In this section, the evaluations of the National Security Framework with the Security Measures and the corresponding controls will be displayed, along with their degree of applicability based on the System Categorization.
Security Measures Evaluations List
When accessing the option, the tool displays a list of the established NSF evaluations, showing by default those that are active.
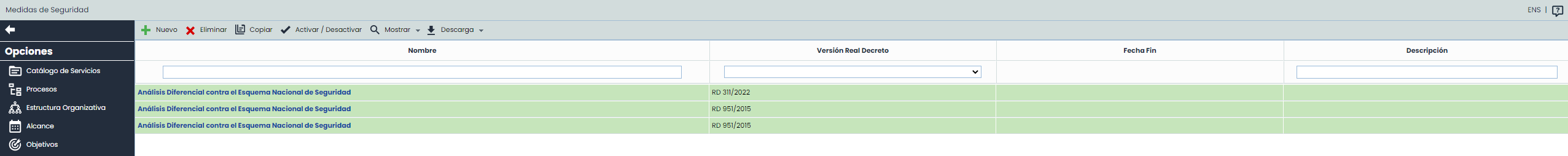
Different actions can be performed in the table, including:
-
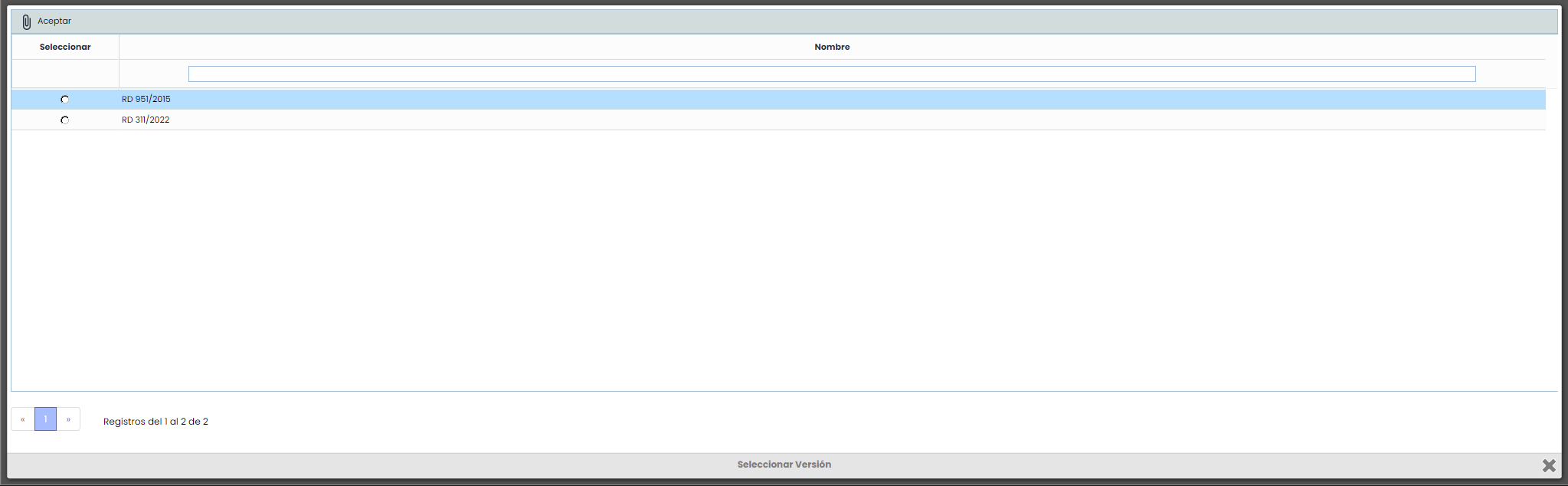
New: Allows creating a new NSF evaluation. By clicking the button, you can select the 2015 or 2022 version of the RD to generate the evaluation.
-
Delete: Allows deleting one or more NSF evaluations, with the possibility of multiple selection.
-
Copy: Allows copying an NSF evaluation with all its information to reuse it.
-
Activate/Deactivate: This option allows performing two different actions:
-
Deactivate an evaluation: when deactivating an evaluation, a historical record of it will be created that cannot be edited. The security level and the degree of applicability of all security measures at that moment will be saved. The buttons for Associate Documentation and Controls will be disabled, as well as editing the End Date.
-
-
Download:
-
Docx Report: A Docx report of the historical evaluation will be generated, which will contain all its information. The report will be available in Pending Downloads.
-

-
Activate an evaluation: you can activate a non-active evaluation. This will allow you to edit the evaluation again and make changes to it.
-
Show: Allows filtering the evaluations in the table:
-
All: Displays all NSF evaluations, both active (shown in green) and historical ones.
-
Active: Only active NSF evaluations will be displayed. This will be the default view.
-
-
Download:
-
CSV Report: A report will be generated with the list of evaluations matching the applied filters. The report will be available in Pending Downloads.
-
Security Measures Evaluation
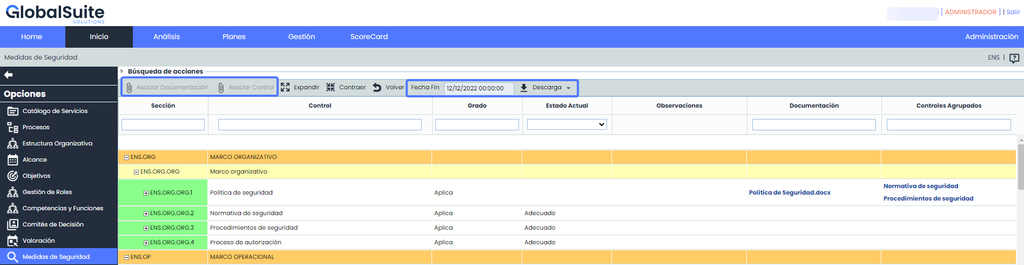
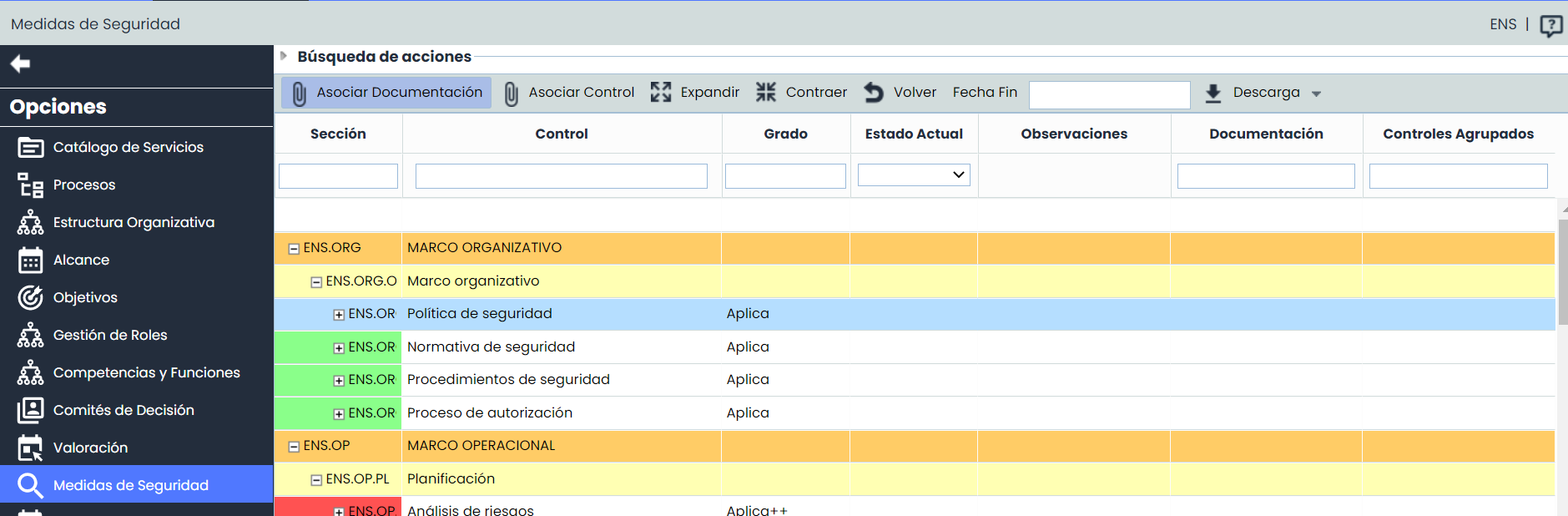
In this view, all the NSF requirements (according to the version selected when creating the evaluation) and the degree of applicability based on the System Categorization will be displayed.
-
Degree: Automatic field calculated based on the System Categorization. It is only editable at the controls level (4th level).
-
Current Status:
-
Editable field only at the controls level, through a dropdown, indicating the status of the requirements or controls.
-
Automatic field only at the Security Measures level (3rd level). The label "Adequate" will be displayed when all applicable controls show a 100% completion degree.
-
NOTE: Controls marked as "Not Applicable" will not be considered when calculating whether the security measure is "Adequate" or not.
Different actions can be performed in the table, including:
-
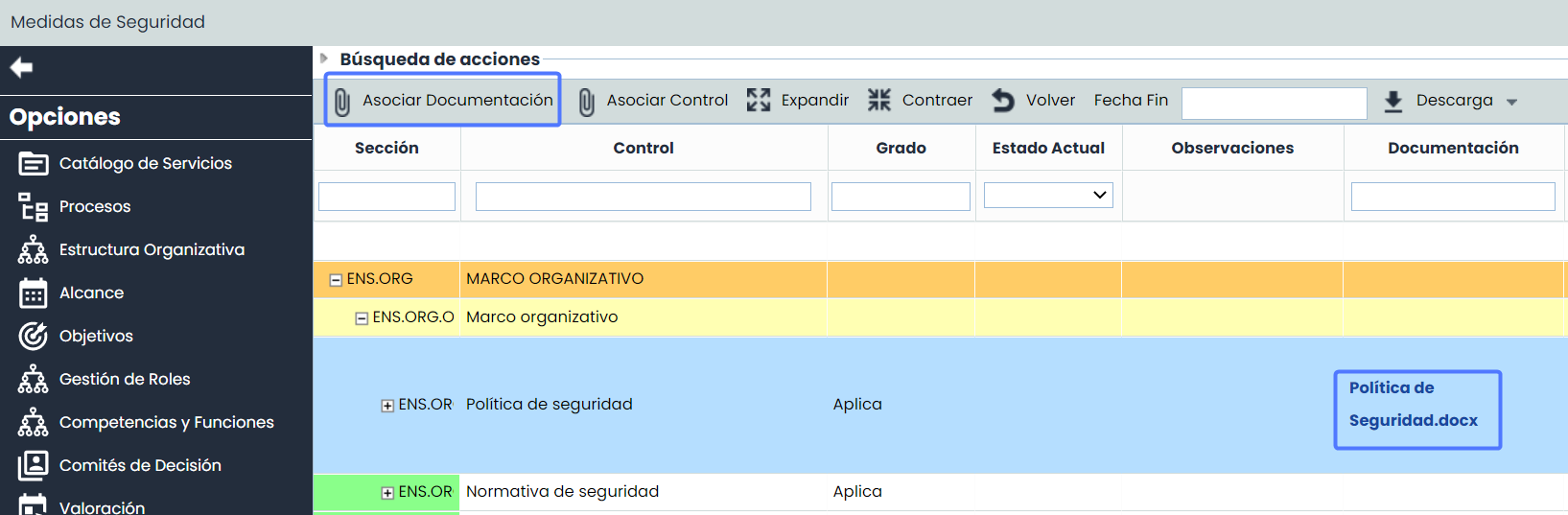
Associate Documentation: Allows associating one or more documents from the document manager to the Security Measures or NSF requirements. To do this, select the desired row and click the "Associate Documentation" button, which will open a window showing the document tree stored in the Document Manager . To associate the documentation, select the checkbox(es) of the desired documents.
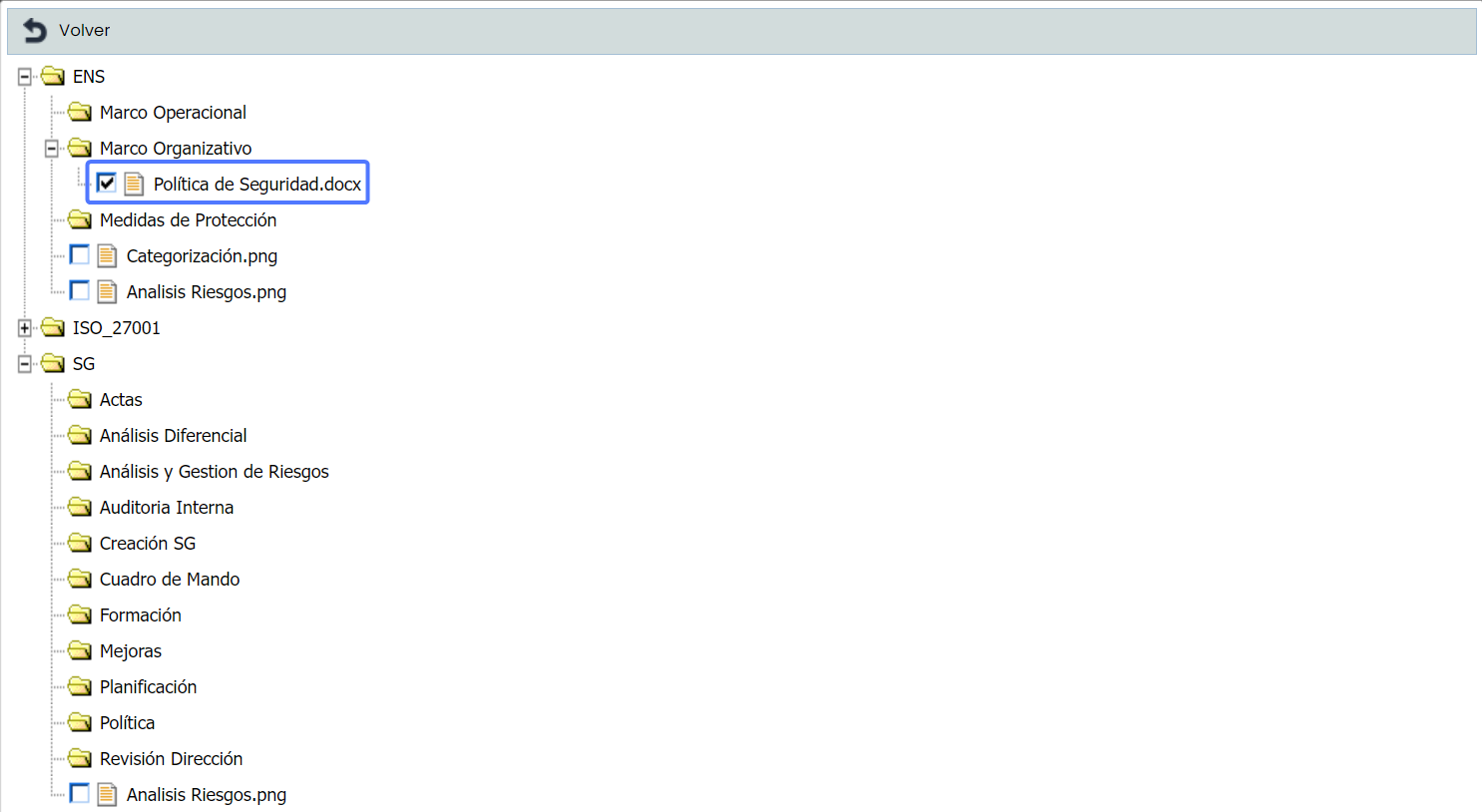
Once the documents are associated, they will be displayed in the corresponding column of the security measure or requirement.
-
Associate Control: Allows associating one or more controls registered in Control Management or in the NSF Adaptation Plan to the requirements to evidence their implementation. To do this, select the desired row and click the "Associate Control" button, which will open the following screen:
-
Expand: Allows expanding the list of actions.
-
Collapse: Allows collapsing the list of actions.
-
Back: By clicking the button, it allows returning to the Adaptation Plans List view.
-
End Date: Field to indicate the review date of the Security Measures.
-
Download
-
Docx Report: A report will be generated with all the evaluation information. The report will be available in Pending Downloads.
-

-
Filters:
-
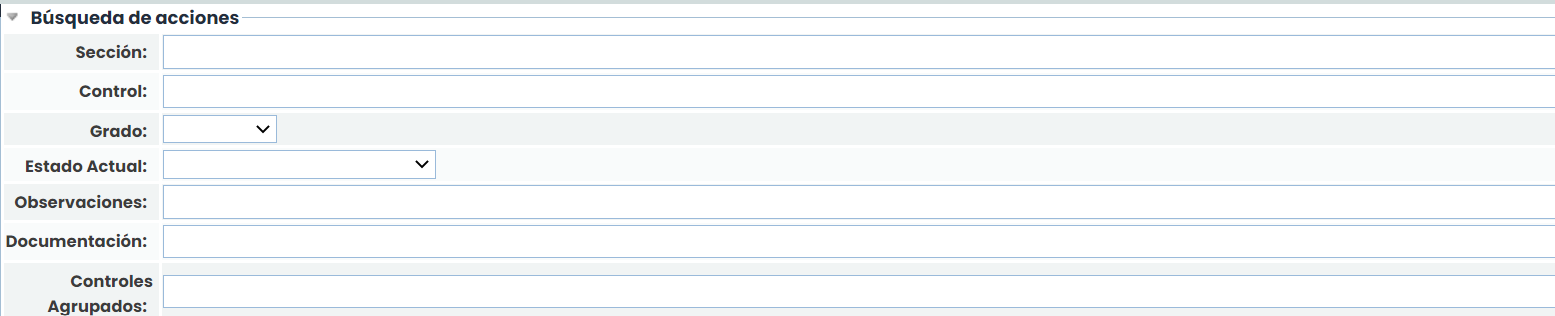
In addition to filtering by Security Measures, it is possible to filter actions independently in the Actions Search section.
-
-
Column visibility: It is possible to adjust column visibility by adding or hiding the desired ones, by right-clicking on the table header.